NOTE Focus list 1 0 11 percent. : You are looking at documentation for an older release. For the latest information, see the current release documentation.
1password 6 8 8 3
1password 6 8 6 – Powerful Password Manager Chrome Extension Stringed 2 8 – Shift Pitch And Manipulate Tempo Loops Left 4 Dead 2 1 0 Skip Tunes 3 2 1 Cookie 6 0 11 Percent Dashlights 2 0 3 Download Free Navicat Premium 12 1 27 The Witcher 2: Assassins Of Kings Enhanced Edition 1 1 Audiofinder 5 9 26 Cm. Oct 14, 2017 1Password is also available for and syncs with Windows, iOS, and Android. Version 6.8.3: The communication between 1Password and the web browsers Chrome and Firefox has been made much more reliable. Fixed a graphical glitch that occurred in detached 1Password mini detail windows affecting some Macs running macOS 10.13. Get 1Password in your browser. 1Password works everywhere you do, including on Linux or Chrome OS. Easily sign in to sites, use suggested passwords, and find what you need. Everything is available at your fingertips. Get to know 1Password in your browser.
The Elasticsearch security features enable you to easily secure a cluster. You canpassword-protect your data as well as implement more advanced security measuressuch as encrypting communications, role-based access control, IP filtering, andauditing.
To use Elasticsearch security features:
Verify that you are using a license that includes the security features.
If you want to try all of the platinum features, you can start a 30-day trial.At the end of the trial period, you can purchase a subscription to keep usingthe full functionality. For more information, seehttps://www.elastic.co/subscriptions andLicense Management.
- Verify that the
xpack.security.enabledsetting istrueon each node inyour cluster. If you are using a trial license, the default value isfalse.For more information, see Security settings. - If you plan to run Elasticsearch in a Federal Information Processing Standard (FIPS)140-2 enabled JVM, see FIPS 140-2.
Configure Transport Layer Security (TLS/SSL) for internode-communication.
This requirement applies to clusters with more than one node and toclusters with a single node that listens on an external interface. Single-nodeclusters that use a loopback interface do not have this requirement. For moreinformation, seeEncrypting communications.
- Generate node certificates for each of your Elasticsearch nodes.
- Enable TLS on each Elasticsearch node.
- If it is not already running, start Elasticsearch.
Set the passwords for all built-in users.
The Elasticsearch security features providebuilt-in users tohelp you get up and running. The
elasticsearch-setup-passwordscommand is thesimplest method to set the built-in users' passwords for the first time.For example, you can run the command in an 'interactive' mode, which prompts youto enter new passwords for the built-in users:
For more information about the command options, see elasticsearch-setup-passwords.
The
elasticsearch-setup-passwordscommand uses a transient bootstrappassword that is no longer valid after the command runs successfully. You cannotrun theelasticsearch-setup-passwordscommand a second time. Instead, you canupdate passwords from the Management > Users UI in Kibana or use the securityuser API.Choose which types of realms you want to use to authenticate users.
- Configure an Active Directory realm.
- Configure a file realm.
- Configure an LDAP realm.
- Configure a native realm.
- Configure a PKI realm.
- Configure a SAML realm.
- Configure a Kerberos realm.
Set up roles and users to control access to Elasticsearch.
For example, to grant John Doe full access to all indices that matchthe pattern
events*and enable him to create visualizations and dashboardsfor those indices in Kibana, you could create anevents_adminroleand assign the role to a newjohndoeuser.Enable auditing to keep track of attempted and successful interactions withyour Elasticsearch cluster:
Add the following setting to
elasticsearch.ymlon all nodes in your cluster:For more information, see Auditing security events Izotope neutron advanced v2. and Auditing Settings.
- Restart Elasticsearch.
By default, events are logged to a dedicated
elasticsearch-access.logfile inES_HOME/logs. You can also store the events in an Elasticsearch index foreasier analysis and control what events are logged. [6.7.0]Deprecated in 6.7.0.
6/8 Simplified
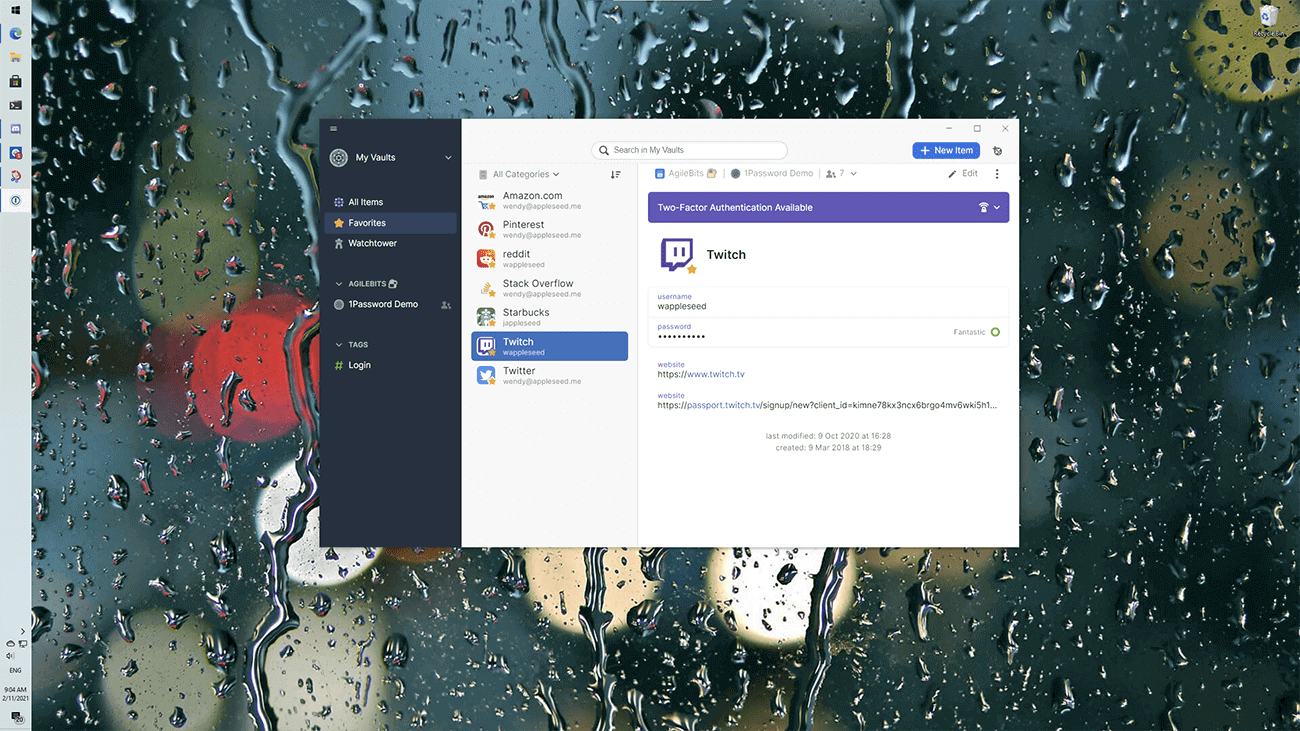
1password 6 8 6 – Powerful Password Manager Chrome Extension Stringed 2 8 – Shift Pitch And Manipulate Tempo Loops Left 4 Dead 2 1 0 Skip Tunes 3 2 1 Cookie 6 0 11 Percent Dashlights 2 0 3 Download Free Navicat Premium 12 1 27 The Witcher 2: Assassins Of Kings Enhanced Edition 1 1 Audiofinder 5 9 26 Cm. Oct 14, 2017 1Password is also available for and syncs with Windows, iOS, and Android. Version 6.8.3: The communication between 1Password and the web browsers Chrome and Firefox has been made much more reliable. Fixed a graphical glitch that occurred in detached 1Password mini detail windows affecting some Macs running macOS 10.13. Get 1Password in your browser. 1Password works everywhere you do, including on Linux or Chrome OS. Easily sign in to sites, use suggested passwords, and find what you need. Everything is available at your fingertips. Get to know 1Password in your browser.
The Elasticsearch security features enable you to easily secure a cluster. You canpassword-protect your data as well as implement more advanced security measuressuch as encrypting communications, role-based access control, IP filtering, andauditing.
To use Elasticsearch security features:
Verify that you are using a license that includes the security features.
If you want to try all of the platinum features, you can start a 30-day trial.At the end of the trial period, you can purchase a subscription to keep usingthe full functionality. For more information, seehttps://www.elastic.co/subscriptions andLicense Management.
- Verify that the
xpack.security.enabledsetting istrueon each node inyour cluster. If you are using a trial license, the default value isfalse.For more information, see Security settings. - If you plan to run Elasticsearch in a Federal Information Processing Standard (FIPS)140-2 enabled JVM, see FIPS 140-2.
Configure Transport Layer Security (TLS/SSL) for internode-communication.
This requirement applies to clusters with more than one node and toclusters with a single node that listens on an external interface. Single-nodeclusters that use a loopback interface do not have this requirement. For moreinformation, seeEncrypting communications.
- Generate node certificates for each of your Elasticsearch nodes.
- Enable TLS on each Elasticsearch node.
- If it is not already running, start Elasticsearch.
Set the passwords for all built-in users.
The Elasticsearch security features providebuilt-in users tohelp you get up and running. The
elasticsearch-setup-passwordscommand is thesimplest method to set the built-in users' passwords for the first time.For example, you can run the command in an 'interactive' mode, which prompts youto enter new passwords for the built-in users:
For more information about the command options, see elasticsearch-setup-passwords.
The
elasticsearch-setup-passwordscommand uses a transient bootstrappassword that is no longer valid after the command runs successfully. You cannotrun theelasticsearch-setup-passwordscommand a second time. Instead, you canupdate passwords from the Management > Users UI in Kibana or use the securityuser API.Choose which types of realms you want to use to authenticate users.
- Configure an Active Directory realm.
- Configure a file realm.
- Configure an LDAP realm.
- Configure a native realm.
- Configure a PKI realm.
- Configure a SAML realm.
- Configure a Kerberos realm.
Set up roles and users to control access to Elasticsearch.
For example, to grant John Doe full access to all indices that matchthe pattern
events*and enable him to create visualizations and dashboardsfor those indices in Kibana, you could create anevents_adminroleand assign the role to a newjohndoeuser.Enable auditing to keep track of attempted and successful interactions withyour Elasticsearch cluster:
Add the following setting to
elasticsearch.ymlon all nodes in your cluster:For more information, see Auditing security events Izotope neutron advanced v2. and Auditing Settings.
- Restart Elasticsearch.
By default, events are logged to a dedicated
elasticsearch-access.logfile inES_HOME/logs. You can also store the events in an Elasticsearch index foreasier analysis and control what events are logged. [6.7.0]Deprecated in 6.7.0.

